Akamai Prolexic
Get in Touch
Get in Touch
Give us a call on 0508 486 372 or fill out the contact form below:
Home » Our Services » Cyber Security »
Prolexic provides organizations with a simple and effective way to protect all web- and IP-based applications in their data center from the threat of DDoS attacks.
Offered as a flexible and comprehensive service, Prolexic Routed stops DDoS attacks in the cloud, well before they reach the data center.
It provides comprehensive protection against the broadest range of DDoS attack types and defends against today’s high- bandwidth, sustained web attacks, as well as the increasing threat of potentially crippling DDoS attacks that target specific applications and services.
Benefits:
Reduce downtime and business risk with fast and effective mitigation of DDoS attacks backed by industry- leading time-to-mitigate SLAs
Protect against the largest DDoS attacks with the globally distributed Prolexic network and 7.8 Tbps of dedicated network capacity
Respond to the most sophisticated attacks with Akamai’s dedicated and highly experienced SOC staff
Reduce costs associated with DDoS protection by leveraging Akamai’s globally distributed cloud security platform
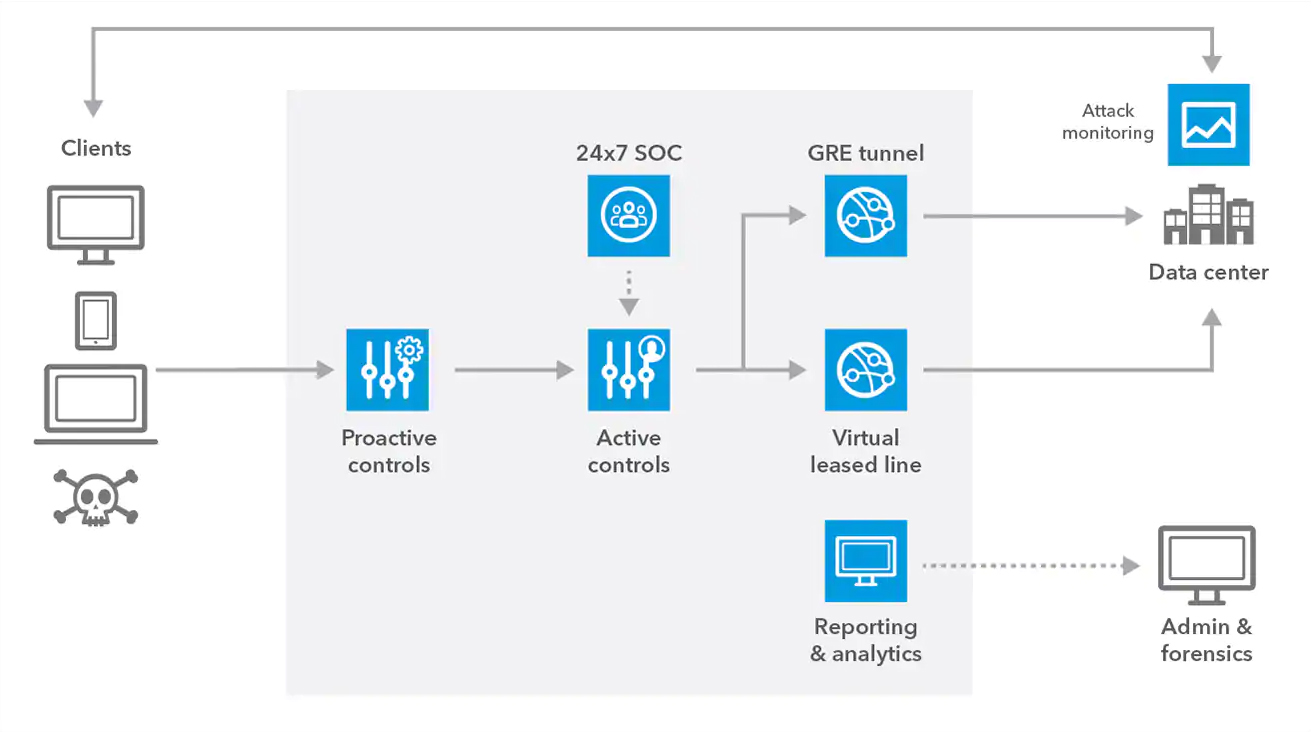
How Prolexic Routed Works
Prolexic Routed is designed to stop DDoS attacks in the cloud, before they reach your applications, data centers, and infrastructure. Network traffic is redirected through Akamai scrubbing centers by making a simple border gateway protocol (BGP) route advertisement change. Akamai offers two deployment options ― always-on is ready to mitigate malicious traffic at all times, and on-demand allows you to redirect traffic when you’re under attack.
Prolexic Routed is built on a DDoS mitigation platform with 18 global scrubbing centers, closer to users and attackers to minimize performance latency and improve network resiliency. Traffic is routed through the closest available scrubbing center, and proactive mitigation controls are architected to drop attacks instantly. Akamai SOC experts analyze the remaining DDoS traffic to quickly and efficiently apply the most appropriate mitigation for every attack vector. Clean traffic is then forwarded to your applications and data centers, and outbound traffic returned directly to users.